Ransomware attacks have only grown bolder as they become more sophisticated threats capable of causing considerable business downtime. Most ransomware in use today is typically spread via phishing emails and designed to penetrate business networks through user devices. Once infected, it doesn’t take long before data on the user device or in SaaS applications becomes encrypted.
Ransomware statistics show that there is a rapid growth of reported ransomware attacks year-on-year. With new variations coming out almost every year, ransomware is continuously being developed to either deceive detection solutions, encrypt different types of files, or convince the user to pay the ransom amount.
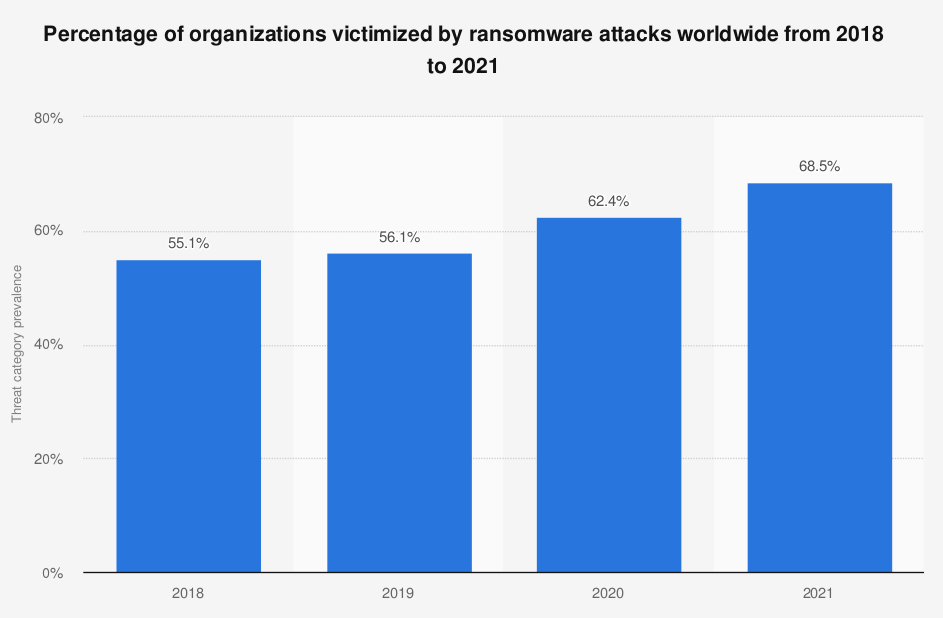
Infographic source: Statista
Below is a non-exhaustive list of ransomware examples in the last decade that have cost organisations millions of dollars. While some may be inactive or have been decrypted by cybersecurity experts, it’s still highly recommended to keep vigilant of any signs of these attacks in case they reappear.
How to Recognise 6 Ransomware Attacks
Before continuing, it may be worth reading this article first to get a better understanding of the type of ransomware that exists, plus some best practices on how to avoid getting infected by ransomware attacks.
The following ransomware examples are some of the most notorious in history. We’ll break down how each of these attacks work, the kind of damage they can inflict, and the ransom demands they expect from affected companies and people.
Ryuk

Ryuk is what cybersecurity experts call “targeted ransomware”. It’s typically used by hackers to attack high-value targets who can afford to pay the ransom to regain access to their system. To get rid of Ryuk, the ransom amount was reported to exceed USD 300,000 in some cases!
Gaining prominence in 2018, the Ryuk ransomware targeted big organisations – over 100 companies – and caused more than USD 60 million in damage worldwide. It spread mainly via malicious emails, containing suspicious links and attachments.
Using military-grade encryption algorithms that are difficult to decrypt, Ryuk infiltrates the system and converts non-executable files in the .ryk file extension. When a user checks the folders that have been processed by Ryuk, they will see a new file – usually named RyukReadMe (.html or .txt) – with ransom demands and guidelines.
To retrieve the encrypted files, the victim will need to send a message to a designated to find out how much they must pay for the decryption key. It’s been reported that the ransom demand could range from 15 to 50 Bitcoins!
WannaCry
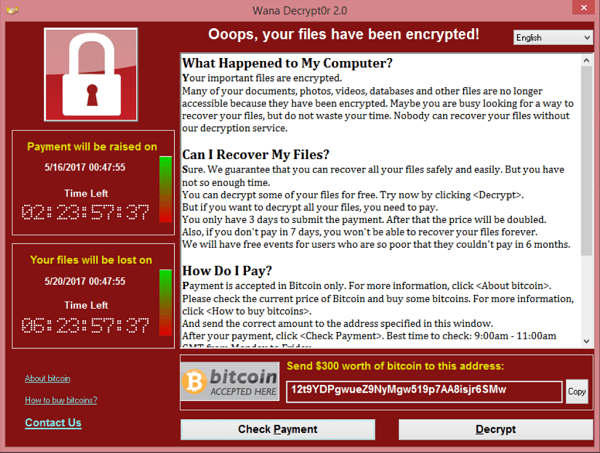
When it was launched in 2017, WannaCry became publicly known as a devastating cyberattack because it was one of the first ransomware to be reported across many news stations worldwide. In terms of financial losses caused by WannaCry, the estimated value at the time was more than USD 4 billion!
Bringing down more than 200,000 systems across 150 countries, WannaCry’s impact was felt in many industries, affecting the likes of FedEx, Nissan, and Telefonica. The amount required to release each infected machine was around USD 300. How did WannaCry even reach this scale of attack?
Like any standard ransomware infection, it started when a user accidentally opened a phishing email and downloaded malware that infected the computer. What was significantly more devastating about WannaCry’s virus, however, was that it spread across other connected computers by using a Microsoft Windows systems vulnerability called Eternal Blue.
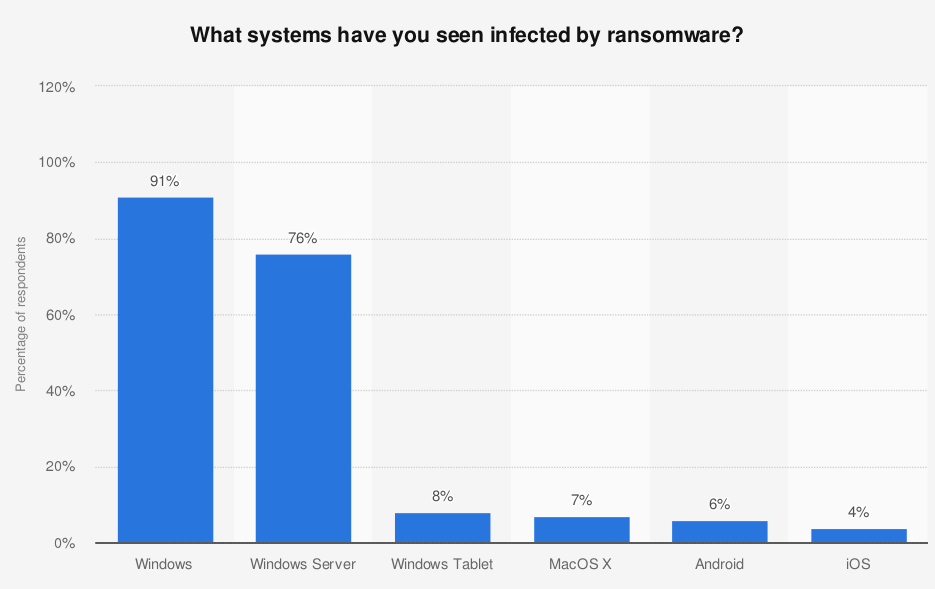
Infographic source: Statista
When experts rushed to fix the problem, they discovered that WannaCry thankfully doesn’t infect all connected computers – only those that have the same Eternal Blue vulnerability. Unfortunately, this meant that the following versions of Windows still have this vulnerability:
- Windows 7
- Windows XP
- Windows 2003
For a long time, no new security patches have been released for these old and outdated versions. This means that any computer still operating these OS are highly vulnerable to today’s advanced malware threats. The hard lesson to take away from WannaCry incident is to always download new patches or update your computer OS.
Petya
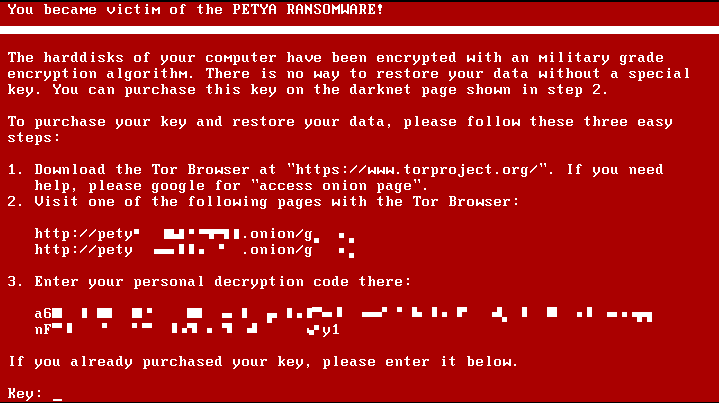
The Petya ransomware was launched back in 2016 and has undergone several different variations since then. It’s estimated that all the Petya variations have caused more than USD 10 billion total in financial losses, affecting organisations in essential industries (i.e., oil, transportation, banks, food) worldwide.
After a user downloads a malicious attachment via a phishing email, Petya encrypts and overwrites files in at least 100 different extensions. Then, it encrypts the computer’s master boot record (MBR) to hijack the normal loading process during the next system reboot. After that, the user will see a ransom demand requesting USD 300 in Bitcoin.
In 2017, however, hackers developed a new version of Petya that used WannaCry’s Eternal Blue exploit to spread itself across infected networks. This upgraded version was named “NotPetya”.
CryptoLocker
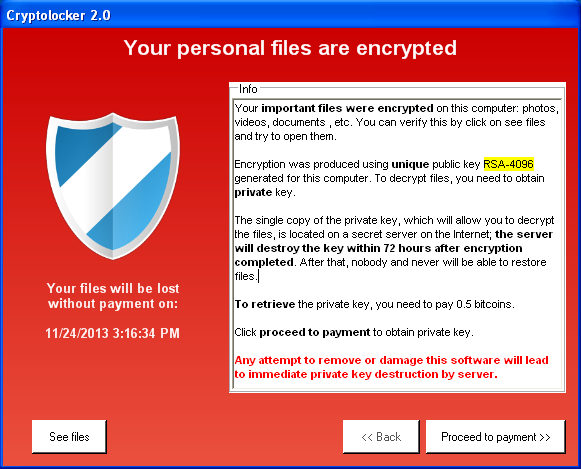
Compared to other ransomware examples on this list, CryptoLocker is an older threat that has not been seen in quite some time. It’s worth inclusion here though, because it was one of the first ransomware of its kind that gained media notoriety.
Extorting money from victims in 2013, CryptoLocker used a large, non-standard encryption key, which stumped cybersecurity experts at the time. This type of ransomware infected more than 200 thousand Windows-based computers when it was distributed via malicious email attachments and via an existing Gameover ZeuS botnet.
Once triggered, CryptoLocker would encrypt files stored on local and mounted network drives using RSA public-key cryptography. A decryption key would be generated in the process and kept on an external server. CryptoLocker then displayed a ransom notification, offering to decrypt the data if a Bitcoin payment was made by a specified deadline and threatening to delete the decryption key if the deadline passed.
In this manner, CryptoLocker managed to successfully extort more than USD 3 million. Fortunately, in late May 2014, the Gameover ZeuS botnet was taken down by Operation Tovar, an international partnership between law enforcement agencies, security companies, and academic researchers. During the operation, CryptoLocker’s database of private keys was seized and used to build a decryption tool to recover the files without paying the ransom.
Related topic: Why Is Encryption Important?
Locky
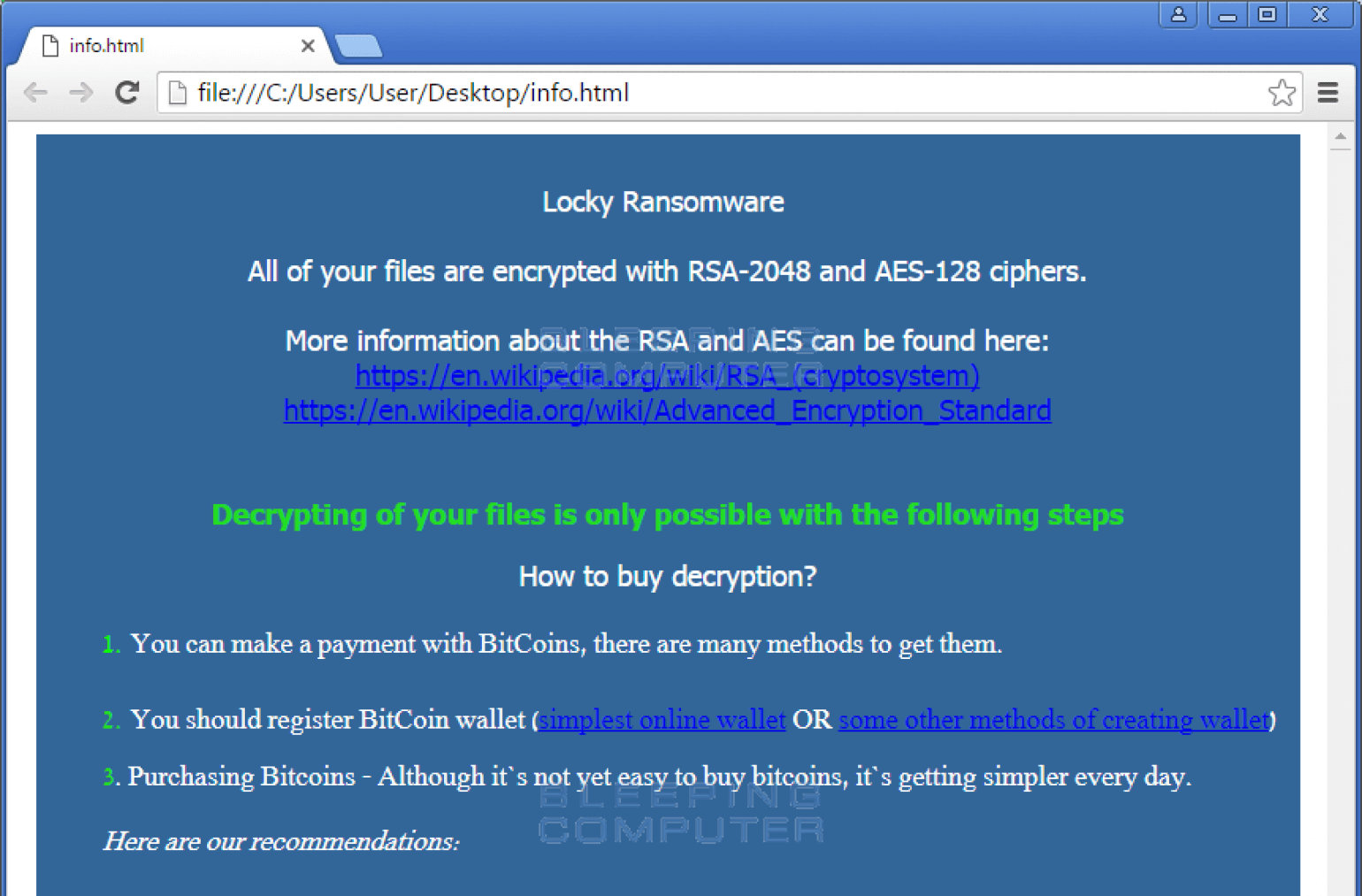
Similar to the CryptoLocker ransomware strain but with more advanced technologies, Locky was released in 2016 and propagated via email. Users would receive an email (allegedly an invoice requiring payment) with an attachment in either .doc, .xls. or .zip formats.
When the user opens this document, they would see gibberish text except for the phrase: “Enable macros if data encoding is incorrect”. If the user enables macros, the document saves and runs a binary file that downloads the actual encryption Trojan horse. Filenames will be converted to unique 16-character letter and number combinations with the .locky file extension. It has been reported that subsequent versions of Locky used other file extensions including .zepto, .odin, .aesir, .thor, .zzzzz, and .osiris.
After encryption, a message would be displayed on the user’s desktop, typically instructing them to download Tor and visit a dark web website for further information. The site would contain the ransom demand and instructions on how to pay between 0.5 and 1 Bitcoin.
What makes Locky complicated to deal with is that, if the infected computer has access to network files, it will encrypt those too. Like CryptoLocker, it’s impossible to decrypt the Locky encryption manually unless a decryption key is owned. These decryption keys are always generated on the malware’s server-side.
Jigsaw
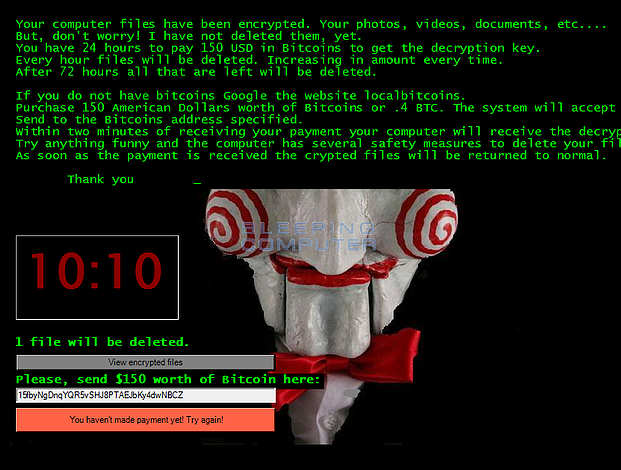
Named after the fictional villain from the horror movie franchise “Saw”, the Jigsaw ransomware was a very real threat for all its victims. This malware was a particularly vicious strain because not only did it threaten to delete encrypted files in case you didn’t pay a ransom, it actually does it.
Jigsaw unleashed its terror through phishing emails with malicious attachments. After a user downloads or opens the attachment, the ransomware infects the system and encrypts more than 200 file types. The user will then get a message with an active countdown stating that they have less than 24 hours to pay USD 150 in Bitcoin before Jigsaw deletes all the affected files.
Unlike other ransomware strains that may have only blocked access to files until payment was made, Jigsaw deleted files progressively, with the amount of deleted files being increased every hour. If the user tried rebooting their computer, the ransomware automatically deletes 1000 files. Jigsaw is truly a nightmare to deal with.
Secure Access to Your Data and Invest in Data Backups
Ransomware can bypass many security solutions because cybercriminals frequently modify and adjust their malware to avoid detection. Plus, the social engineering tactics used to trick victims have also become very sophisticated and hard to detect—even with security education.
That’s why organisations must have a multi-layered approach to ransomware that includes both protection and business continuity. If security measures fail, business continuity is needed for organizations to resume normal operations quickly and avoid costly downtime.
Primary Guard provides a comprehensive selection of cybersecurity products, ranging from Data Protection and Disaster Recovery to Business Endpoint Protection and Access Control Management. Our goal is to minimize cyber threats, improve business efficiency and help maintain your data during or after a disaster occurs.
