In today’s environment, distributed denial-of-service (DDoS) attacks are costly and becoming more frequent. Learning how to fight a DDoS attack and protect your websites and web applications is crucial to the integrity and success of your business.
If you want to improve your company’s security, being capable of preventing a DDoS attack is a must. This article will cover what a DDoS attack is, the types of attacks to be aware of, and the measures that you can take to protect your business from a DDoS attack.
What Is A DDoS Attack?
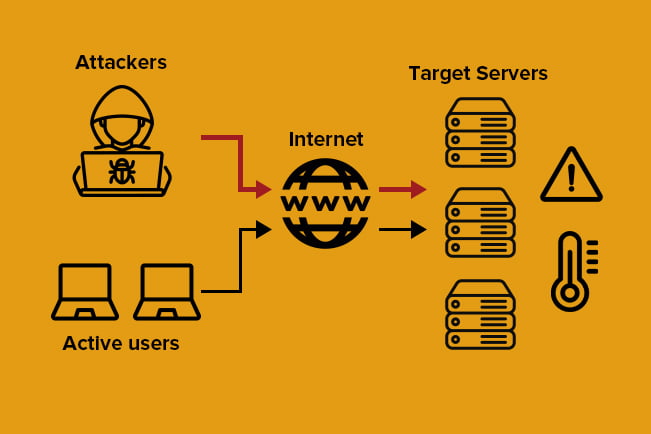
To put it simply, a DDoS attack is a kind of cyberattack where a web server, network, or service is flooded with malicious traffic to pull resources away from processing genuine requests. The origin of this malicious traffic is called a botnet, a network of malware-infected computers (bots) controlled from one central point.
Dealing with a DDoS attack can be tricky because botnets are often distributed throughout the world. Getting attacked from multiple traffic sources makes a DDoS attack more difficult to block than if the signal was originating from a single IP address.
If you’re wondering what does a DDoS attack look like, these are key signs you may be under attack:
- Your website is unavailable
- Slow access to websites and services
- Slow access to local and remote files
- An unusual spike in network traffic
Types of DDoS Attacks

Awareness is your best weapon against a range of cybersecurity threats. Preventing a DDoS attack and protecting your business will depend on your understanding of these threats. There are 3 main categories that DDoS attacks fall under: volumetric, protocol, and application-layer attacks.
Volumetric Attacks
This is the most common type of DDoS attack where bots overwhelm the network’s bandwidth by sending false requests to every open port on the system. Due to bots flooding these ports with large amounts of data, the system has to spend time and resources checking every malicious data request. Hence, no legitimate requests are able to get through.
UDP floods and ICMP floods are the two primary forms of volumetric attacks.
- UDP (User Datagram Protocol) refers to the transmission of data without checks. The UDP format is favored among attackers because it lends itself well to fast data transmission.
- ICMP (Internet Control Message Protocol) refers to the communication between network devices. The ICMP format relies on compromised nodes sending false error requests to the target. The target has to deal with these requests, taking attention away from real ones.
Application-Layer Attacks
This type of DDoS attack targets web applications and exploits vulnerabilities to crash the system. The application layer is the top layer of the OSI network model and the one that most users interact with. Attacks through the application layer focus on direct web traffic and takes advantage of HTTP, HTTPS, DNS, or SMTP protocols.
This type of DDoS attack can often be difficult to detect and troubleshoot because it typically makes use of a smaller number of bots. Since it can mimic legitimate web traffic more easily, the server can be tricked into letting the attack through, treating it as nothing more than a higher volume of legitimate traffic.
Protocol Attacks
Protocol attacks are focused on damaging connection tables in parts of the network that deal directly with verifying connections. By sending purposefully slow pings, deliberately malformed pings, and/or partial packets, memory buffers occur within the target, which uses up a lot of resources to try to verify these pings and potentially causes a crash.
Taking advantage of the three-way handshake process for establishing a TCP/IP connection, the SYN flood is one of the most common protocol attacks. Usually, the client sends a SYN (synchronize) packet, receives a SYN-ACK (synchronize-acknowledge), and sends an ACK (acknowledge) in return before establishing a connection.
During the attack, however, the client only sends SYN packets and the server responds with a SYN-ACK, cutting out the third step. Having to wait for a final phase that never occurs, the network has to use up resources in the verification process.
4 Steps for Preventing A DDoS Attack

- Monitor your website traffic
A huge spike in website traffic is one of the main indicators of a DDoS attack. Keeping track of website traffic with a network monitoring tool is recommended because the built-in alerts and thresholds will notify you when a high number of requests is discovered. This helps hasten your response time to begin DDoS mitigation should an attacker target your website.
- Build redundancy into your network infrastructure
Having a resilient infrastructure is a good idea to keep your service up and running as smooth as possible, even through network issues. Spread your servers across several data centers with a good load balancing system to distribute traffic between them. These data centers should be in different regions of the same country, or if possible, in different countries completely.
Distributing your servers geographically makes it much harder for an attacker to successfully attack your network. With such redundancies in place, even if one server gets attacked, this leaves your other servers unaffected and capable of taking on the extra traffic.
- Set up an Anycast network
Once you have your servers set up regionally and/or globally, you can configure your network to route the incoming requests so they’re dispersed across your servers using the Anycast methodology. Anycast is a specific network routing technique that allows multiple machines to share the same IP address.
This means a single destination address can have multiple routing paths to two or more endpoint destinations. Depending on the user’s location, the routers will send their request to the server in the network that is closest. This dispersion of web traffic across a wide array of servers reduces latency and increases redundancy.
- Use a Web Application Firewall (WAF)
In simple terms, a web application firewall, or WAF, is used to filter HTTP traffic between an application and the internet. When an attacker attempts an application-layer attack, the WAF automatically blocks malicious HTTP traffic before it reaches your website. You can filter traffic by configuring policies to determine which IP addresses will be whitelisted or blacklisted.
Getting the Right Tools to Prevent DDoS Attacks

For companies that conduct a large portion of their business online, a DDoS attack can cost significant losses in revenue. Companies are under pressure to prepare adequate preventative measures because cyberattacks are getting trickier to handle.
Primary Guard offers a resilient and scalable DDoS protection and mitigation tool that combines most of the above suggestions into one solution. It prevents malicious traffic from getting through and disrupting your network while allowing the rest of it to remain functional and high-performing.
Contact Primary Guard today to get proper security for your DDoS Protection needs.
