The number of ransomware attacks has risen and they are only getting more dangerous. An attack on internal networks can cost organizations upwards of millions of dollars. Learning how to prevent ransomware attacks can avoid this scenario, especially if sensitive information is in danger of becoming lost and/or stolen.
Companies shouldn’t be asking when will the next ransomware attack happen, but rather, “Have we experienced any breaches today?” Primary Guard is here to show you the most common delivery methods for ransomware, the different ransomware variants, and the ways to prevent ransomware attacks.
How to Protect Myself from Ransomware?
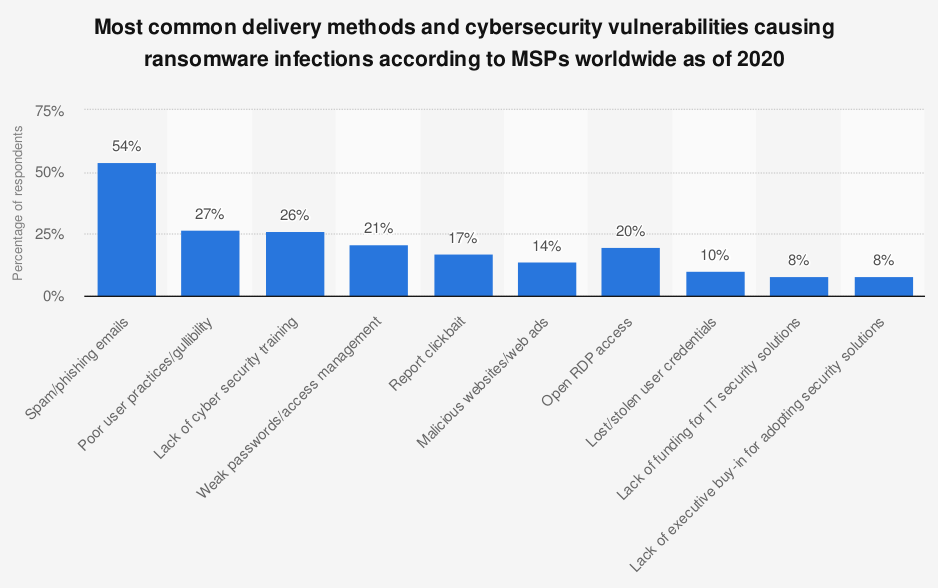
Infographic source: Statista
Government institutions and businesses may use the latest cybersecurity measures, but there is no guarantee that cybercriminals won’t find some weakness to exploit. As long as there is a chance of a big payout, cybercriminals will continue to evolve their strategy and method of attack.
In the event of a ransomware attack, no device that connects to a network or the internet is safe as ransomware can penetrate into your device while you do an online transaction, work online or do any other internet-related activity. Laptops, desktops, mobile devices, IoT devices, and tablets all need safeguarding to prevent ransomware attacks.
According to most reported cyberattacks, ransomware typically spreads via spam, phishing emails, or through social engineering efforts. Social engineering is a psychological manipulation technique whereby people are tricked into opening attachments or clicking on links by appearing as a legitimate, trusted institution.
Another common but more inconspicuous method of a ransomware infection is by spreading through websites or online ads to infect an endpoint device and penetrate the network. Endpoint protection needs to be put in place and taken just as seriously to guard against all attack vectors.
What Are the Ransomware Variants?
These are the 3 main types of ransomware. Take note that, while they are arranged according to severity, none of them are any less dangerous to ransomware victims.
Scareware

A relatively simple form of ransomware designed to trick a user into buying or downloading malicious software. Scareware usually takes the appearance of a fake computer program passing off as security software and/or tech support.
The trap is set by sending unsuspecting victims a pop-up message claiming that malware was discovered on their system and that the only way to get rid of it is to pay up for the fix. A legitimate cybersecurity software firm would not seek potential customers in this way.
When you encounter this kind of pop-up, check the following things:
- Whether you already own this company’s software on your computer. If so, then it should be monitoring your operating system for ransomware infection.
- Whether you only have the free version of the software or you paid for the full package. If it’s the latter, then you shouldn’t have to pay again to have the infection removed, unless your subscription to the service has expired.
If you don’t take the requested action and ignore the message entirely, your files will be safe. However, you must always stay vigilant of scareware attempting to steal your personal information whenever you’re online.
Lock screen viruses

This kind of ransomware is annoying because if it ever gets on your computer, it means you’re essentially locked out of your computer entirely. The virus will lock the user’s computer and display a full-size window with a message stating that the user must pay a ransom to regain access of their computer.
Typically, the message is accompanied with an official-looking seal of a government institution to add legitimacy and urgency. Do not panic and immediately pay.
If you are ever suspected of committing any cybercrimes, real government institutions would not simply demand that a ransom is paid to resolve the situation of your illegal activity. They would go through the appropriate legal channels.
Ransomware encryption

The most damaging ransomware used by cyber criminals is to seize your files and encrypt them, demanding payment in order to get the files decrypted and restored. Once it encrypts files, it is very difficult for security software to return them to you.
The reason why this type of ransomware is so dangerous is because it is actually a cryptovirus – a virus that uses cryptography in combination with malware to lock computer files. This method of attack allows a hacker to infiltrate a computer’s data and file structure, encrypting every file and folder.
If this ever occurs to you, your files are essentially gone until you pay the ransom to decrypt the encrypted data. Be warned that even if you do pay up, there’s no guarantee the cyber criminals will give you those files back. Proactive data protection and data backup solutions are your best bet to recover your data and avoid infected files.
Related topic: Why Is Encryption Important?
Best Practices to Prevent Ransomware Attack
Our cybersecurity experts at Primary Guard suggest organizations take several of the following precautionary measures to prevent ransomware attacks:
- Conduct awareness training to educate employees on how to identify any potential issues immediately. Update everyone on the latest email phishing attack and social engineering aimed at turning victims into abettors.
- Coordinate a response with other parts of your organization including finance, communications, and the executive team to respond when ransomware hits.
- Ensure your incident response and business continuity plan includes ransomware response protocols.
Revise Cybersecurity Protocols
Your IT department or staff responsible for IT security should also implement the following regulations:
- Leverage multi-factor authentication for all users, starting with privileged, administrative and remote access users.
- Grant access and admin permissions based on need-to-know and least privilege.
- Enable automatic updates for all operating systems and third-party software.
- Implement secure configurations for all hardware and software assets.
- Remove unsupported or unauthorized hardware and software from systems.
- Leverage email and web browser security settings to protect against spoofed or modified emails and unsecured webpages.
- Create application integrity and whitelisting policies so that only approved software is allowed to load and operate on your systems.
Develop A Comprehensive Plan of Recovery from Ransomware
In the worst-case scenario where a system restore is not viable and/or the ransomware infection is too widespread, an organization needs to have alternative means to restore files:
- Maintain inventories of critical or sensitive information.
- Establish regular automated backups and redundancies of key systems.
- Use disconnected external storage devices or the cloud to keep data backups stored in locations seperate from any potentially infected systems and prevent them from being accessed by the ransomware.
Avoid the Loss of Information Critical to Business & Operations
At the end of the day, the best response to a ransomware attack is to avoid becoming a victim of one in the first place. Organizations both large and small need to back up their data regularly and securely so that downtime and data loss will be minimal or none if you ever suffer an attack.
Primary Guard provides a comprehensive selection of cybersecurity products, ranging from Data Protection and Disaster Recovery to Business Endpoint Protection and Access Control Management. Our goal is to minimize cyber threats, improve business efficiency and help maintain your data during or after a disaster occurs.
