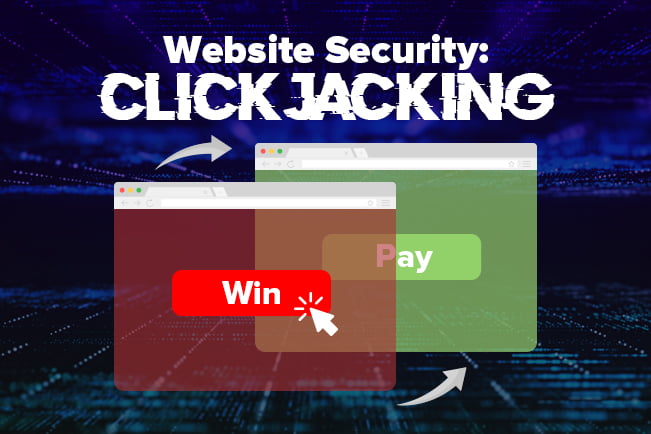
What is Clickjacking?
The purpose of clickjacking (“click hijacking” in its full terminology) is to trick a PC, tablet, or smartphone user into clicking an invisible webpage or HTML element – typically a button or a link – when they intended to click on something else on a webpage.
Also known as a “UI redress attack”, an attacker uses multiple transparent or opaque layers to “hijack” clicks intended for the decoy website and route them to the target website. This other site could be a malicious page or even a legitimate page – for example, a page on the user’s banking site that authorizes the transfer of money.
Keystrokes can also be hijacked through a similar technique. A user can be tricked into thinking they’re typing their password into their email or bank account when they’re instead typing into an invisible iframe controlled by the attacker.
How dangerous is a clickjacking attack? These are the versatile ways clickjacking can be employed:
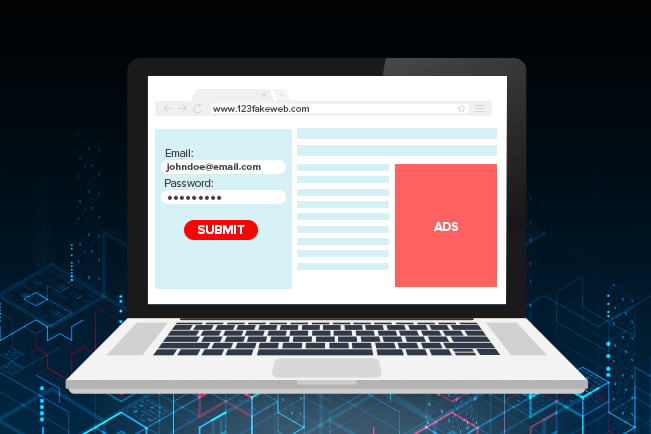
- Harvest login credentials or other sensitive information, by rendering a fake login box or sign-up form on top of the real one.
- Spread worms on social media sites like Twitter and Facebook.
- Spread malware by redirecting unsuspecting users to malicious download links.
- Purchase products online of an undisclosed amount or quantity by tricking people into clicking on things they otherwise would not.
What Does a Clickjacking Attack Look Like?
Clickjacking attacks use CSS to carefully create and manipulate stylesheets, iframes, and text boxes. Typically, the attacker incorporates the target website as an iframe layer overlaid on the decoy website.
Using the appropriate width and height position values, the target website iframe is positioned within the web browser so that there is a precise overlap of the target action with the decoy website, regardless of screen size, browser type, and platform.
In more technical terms, the z-index is one to pay attention to as it determines the stacking order of the iframe and website layers. The attacker can select the opacity value to be defined as 0.0 (or close to 0.0) so that the iframe content is transparent to the user.
However, clickjacking is not just one specific attack, but a broad family of attack vectors and techniques. In particular, overlay-based attacks are the most popularly used by hackers. These are some of the main categories of overlay-based clickjacking:
- Complete Transparent Overlay
Another method of clickjacking where a transparent legitimate page (called a tool page here) is overlaid over a carefully crafted malicious page. By setting a higher z-index value, an invisible iframe – in which the tool page is loaded into – is positioned above the visible page.
- Cropping
The attacker overlays only the selected controls from the transparent page on the visible page. Depending on the goal of the attack, this could be applied in a myriad of ways from covering buttons with invisible hyperlinks to trigger a different action to replacing button labels with false commands.
- Click Event Dropping
For this attack, the legitimate page is displayed in the foreground, completely obscuring the malicious page behind it. The CSS pointer-events property of the top is set to none. This means that click events will “drop” through the overlaid legitimate page, so the user’s actions only register on the malicious page below.
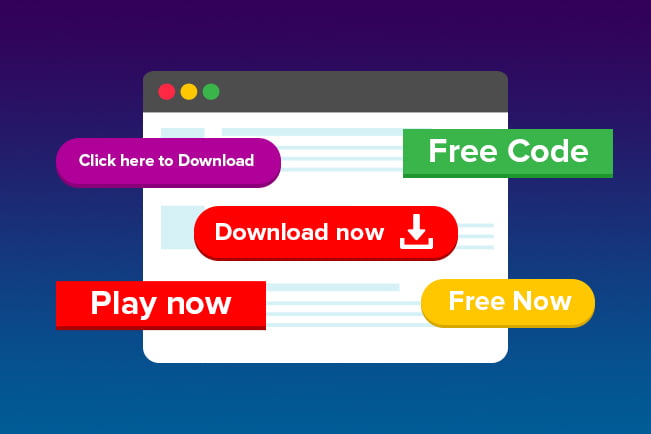
Type of Clickjacking Attacks
Like there are several techniques for clickjacking, there are also many forms it can take. Here are the most common variants:
- Likejacking: The users’ clicks are redirected to “likes” on a Facebook page or other social media networks.
- Cookiejacking: The user is led into providing the attacker with cookies stored on their web browser, which means the attacker can see what websites the user has visited and perform actions on behalf of the user.
- Filejacking: The user is tricked into giving the attacker access to their local file system to take files.
- Cursorjacking: This technique involves the cursor position being changed to a different place from where the user perceives it. While the user believes they’re making a certain action, they’re actually making a different one.
- Password manager attacks: Rather than a direct attack on the user, this form of clickjacking deceives password managers instead by taking advantage of their auto-fill functionality.
How to Mitigate Clickjacking Vulnerabilities

To ensure that your website doesn’t fall victim to a clickjacking attack, you need to make sure your web pages cannot be abused by an unauthorised party for malicious purposes. In most cases, you can prevent clickjacking by inputting browser instructions directly via these two ways.
X-Frame-Options HTTP Header
The X-Frame-Options HTTP header can be used to define whether or not a browser should be permitted to render a page in a <frame>, <iframe> or <object> tag. Designed specifically to counter clickjacking attempts, there are 3 permitted values for this header:
- X-Frame-Options: deny
Regardless of what an external party intends to do, the page cannot be displayed in a frame.
- X-Frame-Options: sameorigin
The page can be displayed in a frame, but only on the same website as the page itself.
- X-Frame-Options: allow-from *uri*
The page can be displayed in a frame, but only in a specific URI (a named website).
Content-Security-Policy (CSP) HTTP Header
The Content-Security-Policy HTTP header provides a broader range of protection against clickjacking than the X-Frame-Options header. This is because it was initially developed to handle XSS and other data injection attacks. Website authors can whitelist individual domains from which resources (like scripts, stylesheets, and fonts) can be loaded and also domains that are permitted to embed a page.
The frame-ancestors directive will need to be included in the following instructions to control where your site can be embedded.
- Content-Security-Policy: frame-ancestors ‘none’
Regardless of what an external party intends to do, the page cannot be displayed in a frame.
- Content-Security-Policy: frame-ancestors ‘self’
The page can be displayed in a frame, but only on the same website as the page itself.
- Content-Security-Policy: frame-ancestors *uri*
The page can be displayed in a frame, but only in a specific URI (a named website).
How to Check If Your Website Is Vulnerable to Clickjacking
To fully defend a website against clickjacking attempts, however, is not an easy task and requires vigilance from IT specialists. Do not take clickjacking likely as it’s not the end goal of the attack; it can be the means of launching many more damaging attacks to do virtually anything possible via webpages.
If you’re unsure of the security of your website, then check out Scantrics.io’s FREE Website Vulnerability Scanner. Scan your website regularly for security misconfigurations or vulnerabilities. Besides checking for possible clickjacking attacks, the tools that are on Scantrics.io are dedicated to providing all kinds of in-depth vulnerability assessments for web applications.